Make sure your company is protected from ransomware with these 6 tips on ransomware prevention.
I’ve heard this question a few times in recent months and unfortunately that’s a few times too often. Most computer users these days are familiar with viruses which date back to the days of floppy disks and DOS. Over the years viruses have evolved in many directions and have out grown that simple descriptive name. The more common term used these days to describe software that causes unwanted activities or actions is Malware. Malware includes anything from adware (software that creates those annoying popups when you browse the Internet) to rootkits (software that you can’t usually tell is on your computer collecting passwords and banking information) to the latest threat: Ransomware.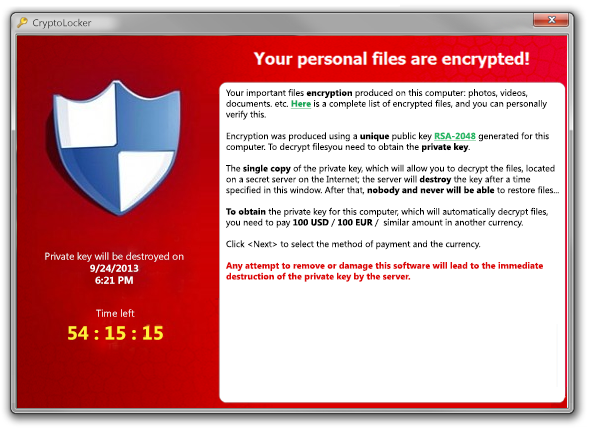
Ransomware. So what is it?
Ransomware is a type of malware that installs itself on a computer then searches out any files it can see either locally or on a network share, then encrypts those files with a very strong encryption algorithm rendering them inaccessible to users. The software then presents the user with a ransom note asking for payment to unencrypt the files. The initial detections of ransomware date back as far as the late 1980s and evolved over the years but did not have nearly as big an impact as CryptoLocker and CryptoWall have in recent years. This new generation of ransomware uses very strong encryption and requests that the ransom be paid in bitcoin which is difficult to trace. There have been reported cases where business owners have paid very high ransoms only to be further extorted and sometimes never receive the key to recover their files. There has been some success in breaking the encryption on some infections but with the pace of change in the malware code and the use of ever stronger encryption there has been a very low success rate.
What do I do about it?
- Don’t get infected.
- See number 1.
Any decent network administrator will have antivirus software running and up to date on all of their systems, and that’s an important piece of the security landscape, but it should not be considered the only line of defense. Malware, including ransomware, can infect systems in a number of ways. Arguably the most common method of infection is a network user clicking a link or opening a file in an email. The file contains Trojan code that starts executing immediately and doesn’t give any indication to the user that they’ve caused a problem until it’s too late. Websites can also contain malicious code and infect systems when users browse to them. In both these cases, antivirus software can sometimes catch the Trojan but not always. As I mentioned earlier, the code is constantly being modified so that antivirus engines can’t recognize it. There have also been versions of ransomware that search the internet for vulnerabilities to access servers and infect them without user intervention.
Prevention = Protection. But how exactly?
To properly protect your systems and, more importantly, your data from this threat you need:
- Consistent, up-to-date protection in the form of good antivirus software with on-access scanning. On-access scanning checks each file, as it is executed, to see if it contains known malicious code.
- It is also important to install operating system and application security updates on a regular basis. The software vendors find out about vulnerabilities and patch them just as the hackers exploit them so keeping up to date is critical.
- To harden your network from external threats, close any “well known ports” such as RDP and have remote users connect using a VPN or non-standard port instead.
- Ensure that all users have complex passwords to protect against the use of a password guessing program to gain access as well.
- The most important piece of protection is education. Make sure your users are aware of this type of threat and the potential ways that they could be tricked into opening an infected file. If it’s not a file you’re expecting or it seems odd in any way then don’t open it!
Ultimately, there’s only so much you can do to protect yourself from ransomware and malware in general. It’s always possible that an email will get through that looks close enough to something that was expected just before the antivirus engine gets updated and… it’s too late.
- The best and final line of defense against ransomware is a good current backup with multiple versions. Daily backups with rotating storage media is a minimum for any business. More frequent incremental backups will allow for faster remediation and reduced data loss in the event of a failure. There are devices that can take very frequent backups throughout the day, allowing a point-in-time restore, to just before an infection occurred, almost instantly. An infection reported in the middle of the afternoon could be isolated to a PC by identifying the user account that encrypted the files, then repaired and restored with a minimal loss of data and work.
While I’ve been directing the IT Services team at Vision33, we’ve encountered and successfully ridden ransomware from companies looking to access to their critical data and get back to business. My goal with this blog is to increase awareness and reduce incidents of ransomware infection. For further information, to help with a ransomware infection, or for any IT needs, please contact us to assist with your IT requirements. Connect with us at contact@vision33.com or 604.473.2100.



