Vision33 Ranked on Accounting Today’s VAR 100 List For 15th Consecutive Year
SAP Business OneThe publication’s editorial team ranks the top resellers of accounting software based on their...
March 16, 2016
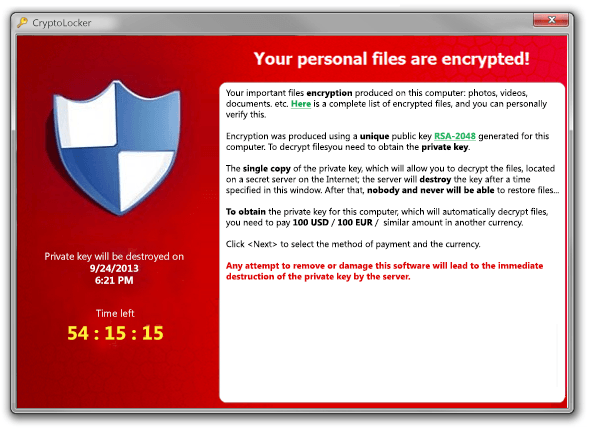
Blog > What is RANSOMWARE? And 6 ways to protect your business
I’ve heard this question a few times in recent months and unfortunately that’s a few times too often. Most computer users these days are familiar with viruses which date back to the days of floppy disks and DOS. Over the years viruses have evolved in many directions and have out grown that simple descriptive name. The more common term used these days to describe software that causes unwanted activities or actions is Malware. Malware includes anything from adware (software that creates those annoying popups when you browse the Internet) to rootkits (software that you can’t usually tell is on your computer collecting passwords and banking information) to the latest threat: Ransomware.
Ransomware is a type of malware that installs itself on a computer then searches out any files it can see either locally or on a network share, then encrypts those files with a very strong encryption algorithm rendering them inaccessible to users. The software then presents the user with a ransom note asking for payment to unencrypt the files. The initial detections of ransomware date back as far as the late 1980s and evolved over the years but did not have nearly as big an impact as CryptoLocker and CryptoWall have in recent years. This new generation of ransomware uses very strong encryption and requests that the ransom be paid in bitcoin which is difficult to trace. There have been reported cases where business owners have paid very high ransoms only to be further extorted and sometimes never receive the key to recover their files. There has been some success in breaking the encryption on some infections but with the pace of change in the malware code and the use of ever stronger encryption there has been a very low success rate.
Any decent network administrator will have antivirus software running and up to date on all of their systems, and that’s an important piece of the security landscape, but it should not be considered the only line of defense. Malware, including ransomware, can infect systems in a number of ways. Arguably the most common method of infection is a network user clicking a link or opening a file in an email. The file contains Trojan code that starts executing immediately and doesn’t give any indication to the user that they’ve caused a problem until it’s too late. Websites can also contain malicious code and infect systems when users browse to them. In both these cases, antivirus software can sometimes catch the Trojan but not always. As I mentioned earlier, the code is constantly being modified so that antivirus engines can’t recognize it. There have also been versions of ransomware that search the internet for vulnerabilities to access servers and infect them without user intervention.
To properly protect your systems and, more importantly, your data from this threat you need:
While I’ve been directing the IT Services team at Vision33, we’ve encountered and successfully ridden ransomware from companies looking to access to their critical data and get back to business. My goal with this blog is to increase awareness and reduce incidents of ransomware infection. For further information, to help with a ransomware infection, or for any IT needs, please contact us to assist with your IT requirements. Connect with us at contact@vision33.com or 604.473.2100.
Subscribe to our newsletter to receive our latest blog posts, case studies and ERP news delivered straight to your inbox.
The publication’s editorial team ranks the top resellers of accounting software based on their...
GROW with SAP is underpinned by its predictable, cost-effective, and rapid implementation and the...
The team will drive global demand programs, blend digital engagement with real...
Recieve our latest blog posts, case studies, and ERP news
delivered straight to your inbox.